Cat And Mouse — ESEA Anti-Cheat
As the industry-leading anti-cheat platform, ESEA works diligently to ensure fair gameplay on the ESEA platform and sets the standard for anti-cheat technology.
The ESEA Anti-Cheat team often works on updates that many users do not see unless you are involved in the cheating scene. Most people outside of the Anti-Cheat team at ESEA are not privy to detailed updates regarding anti-cheating functionality. However, this update is essential for the competitive esports and Counter-Strike community and provides a small glimpse inside of the latest ESEA anti-cheating operation.
Three years ago
About three years ago, the ESEA Anti-Cheat team started working on updates to strengthen its capabilities, forcing the cheat development scene to evolve. With the advent of new and popular games deploying anti-cheating techniques at launch day, along with ESEA's advancement of cheat prevention and detection layers, the cheating industry and scene became more profitable and advanced.
Around the same time, ESEA started to notice the use of software techniques and exploits that have primarily been utilized in malware development to attempt to evade ESEA's anti-cheat technology. Up until this point, the most sophisticated cheating techniques that were active on the ESEA platform included:
- Using vulnerable drivers to load priviledged code
- Network packet sniffing, injection, and game traffic decryption
Let us focus on the last point: network packet sniffing, injection, and game traffic decryption. One method utilized rudimentary hardware. It was simple enough: use single board computers and microcontrollers (e.g., Raspberry Pi and Arduino) to sniff and decrypt game traffic in a Man-in-the-Middle attack, and at times, inject into the network stream. After investigating these network-based attacks, the ESEA Anti-Cheat team was able to:
- Deploy detections resulting in "fingerprinting" the devices that were being used to perform the attacks
- Deploy prevention layers to stop this from taking place in the future
- Ban the cheaters, including the developers based on detection data procured throughout the investigation
Present day
Three years later, today, we see a more sophisticated hardware-based attack. Many people in the competitive Counter-Strike scene have likely heard about cheating scandals, where teams and players have admitted to using hardware cheats on LAN, for example. The method primarily discussed is a DMA (Direct Memory Access) attack.
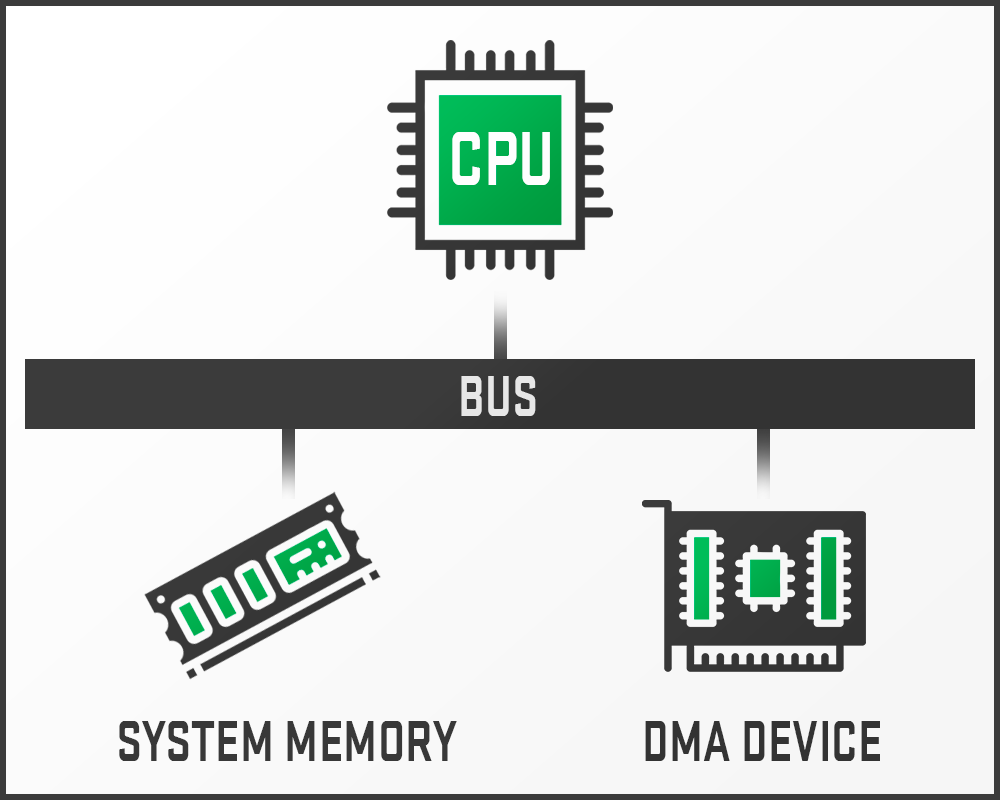
This attack requires additional hardware that reads directly from the memory bus via a PCI Express lane. For simplicity, the following is an example of how the attack would work in a cheating scenario:
- The cheater has two PCs: one running the ESEA Client and Counter-Strike (called Client PC) and another parsing data (called Attack PC)
- Client PC has a DMA device plugged into a PCI Express slot
- USB cable connects the PCI device from Client PC into Attack PC
- Attack PC parses data gathered from DMA device plugged into Client PC
- Attack PC sends data, such as player positions to a Raspberry Pi, of which allows a phone to connect via WiFi and draw player positions on phone
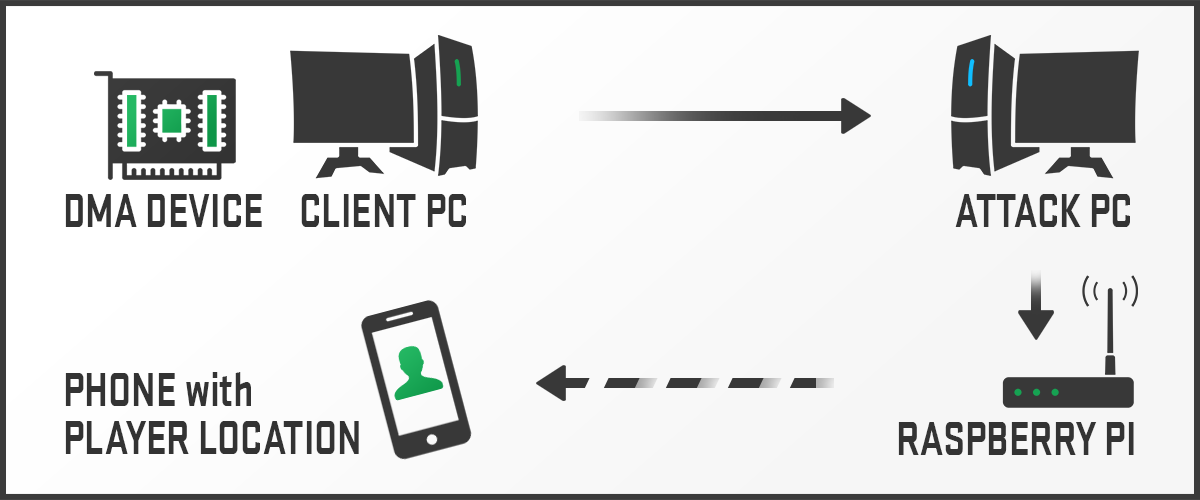
In the above attack scenario, the attack requires two PCs and a Raspberry Pi. The attack example shows only reading data from memory that avoids software-based detections from most anti-cheat tools. The attack scenario above can be modified to not only read memory via DMA but also write to memory. Writing to memory could result in aim assistance, for example.
DMA attacks have been around for quite some time in the malware and forensic security industry. Due to the evolution of the cheating scene as mentioned previously, DMA attacks are now the new trend in the more sophisticated cheat developer communities. This method of hardware-based cheating is boasted as undetectable, though ESEA has been monitoring this trend and working for many months on detecting this method of cheating.
Detecting the undetectable
Throughout the recent months, the ESEA Anti-Cheat team has been developing multiple detection techniques to combat hardware-based cheats. ESEA's Anti-Cheat team has been able to detect and monitor the ongoing development of several cheat providers and developers as they tinker, tweak, and even sell their cheats to customers attempting to break into the competitive, semi-professional, and professional Counter-Strike scene.
These hardware cheats are expensive. The developers usually have malware development, embedded systems, hardware engineering, or, in some cases, electronic music backgrounds. The hardware required for the cheats to function usually is in the form of single boards or entire development kits. Given the hardware costs between hundreds of dollars on the low end, and around one thousand on the high end, along with the expertise of the developers required to create such products, prices for these cheats have been seen in the $1,500 to $5,000 range.
In the media, accusations and cheating scandals in competitive Counter-Strike have featured leaked pictures of DMA hardware. While the pictured hardware can be used in a DMA attack, the specific device featured in the media is starting to become less popular in the cheat scene, primarily due to the inability to easily modify its hardware identifiers. Other hardware devices used are detected by the ESEA Client using more sophisticated methods, regardless of if the device attempts to spoof itself as another legitimate device or not.

As a result of many months of research, development, and intelligence gathering, ESEA has been in the midst of a ban wave of both cheat customers and developers using and testing hardware-based cheats. The ESEA Client can detect hardware-based cheats even when disguising the hardware cheat as a legitimate device. The detection methods utilized by the ESEA Client play only one small role in the ESEA Client's cheat detection layer for hardware-based cheats and do not touch on the anti-cheat's prevention layer.
At the end of the day, we hope this post is insightful to other anti-cheat platforms to recognize that this threat is real, so they can work on solutions to protect their users.
Although it is a standard practice for other companies to place manual cheating bans, ESEA Anti-Cheat convicts cheaters only based on detection data. The recent advancements in the cheating world further highlights why ESEA's anti-cheating technology is used not only within the ESEA platform, but protects the ongoing Minor qualifiers, Intel Extreme Masters, and other events. ESEA Anti-Cheat also protects and ensures fair gameplay in the growing professional scene (Mountain Dew League and ESL Pro League).
While it may seem like the easy way to break into the highly competitive Counter-Strike and esports scene, cheating on ESEA, regardless of how sophisticated the cheating method may be, will result in an eventual cheating ban that will follow the punished user's esports career for life.
GL, HF.
